
It's been a while since Sofie Mustermann bothered about her keys. She doesn't bother about cash or credit cards either, and certainly not about tickets for theatres or airplanes or anything. When she reaches her front door or the door to her office, it automatically opens. When she wants to start her car, she pushes a button. In shops and supermarkets, she simply grabs the goods and puts them in her shopping cart and never stops at the till. She never buys a ticket for the train or the airplane, and at the airport, she doesn't bring her passport, never notices the customs area. She even boards without a pass.
Sofie can use any computer screen that she passes by as if it were her own. The moment she stands before it, it turns into a window to her personal data and the set-up will invariably match her usual preferences.
Sofie never gets lost, she always knows exactly where she is. She knows - or she can immediately locate information on - most of the buildings and objects that surround her. She knows which other people are around her, , and if there is anybody among them that she should talk to.
On the other hand, they also know a great deal about Sofie - even if they may never have met her before. The reason being that today almost all people, objects, buildings and pets carry a digital tagging which means that everybody can see a lot more than what actually meets the eye.
Most people call it an ”aura” - and that's not a bad description at all. Many religions talk about an invisible field of radiance that extends beyond the body of any living creature. In much the same way, an extra layer of information has been added to the world during the past few decades; a new presence in a kind of parallel digital world where everything and everybody are connected and visible to each other in every little detail.
Denmark and the Baltic group of countries in the European Union were the first major areas in which governments offered ID implants for all children on a regular basis - similar to the state sponsored vaccinations. At their child's 24 months medical exam, most parents choose to have the tiny chip inserted under the soft skin near the child's collarbone. The operation is done under local anesthesia, and it's otherwise completely harmless: The chip is smaller than a grain of rice and it's inserted by means of a syringe in no time.
The chip is extremely simple. In most cases, in contains only one piece of information: a unique serial number that identifies the person. The chip can be read by special wireless readers within a distance of up to 8 meters, depending on the type of reader.
According to the Danish Home Office, almost 96% of the population above the age of two years now carry an ID implant. The ambition is to arrive at 99% within the next three years. ”There will always be a small group of individuals who for one reason or another will not under any circumstances want to have the ID implant - and obviously, they have every right to refuse it. All we can say is that they certainly do make things very complicated for themselves”, says Flemming Force from the Home Office.
Cheap chips
The first applications using RFID technology, - short for ”Radio Frequency Identification” - as it was called at the time, were launched around the turn of the millennium, but price prevented the chip from winning truly widespread application.
So initially the wireless readable ID chips were not used for tagging merchandise - instead they were used as a means to identify or endorse human beings. It was basically the same technology that early on made it possible for skiers to leave their ski passes in their pockets when they sat on the ski lift and allowed cars to cross bridges or enter urban zones without having to stop to pay the tolls.
The real breakthrough did not come until the price of marking an object had dropped to only a few cents - around the same time that it became possible to print electronic circuits directly onto the merchandise using conductive ink and resin.
By 2014, the number of RFID coded goods had reached a level that inspired COOP to open the first Danish supermarket with only one check-out counter for manual payment. By far, most of the customers preferred to have their goods automatically scanned at the exit and to subsequently use their mobile to approve that the amount would be drawn on their account.
This was at about the same time that RFID readers began to enter the private households. Equipped with a tag-reader, the fridge would “sense” the articles in it, the washing machine would know the right temperature for the next pile of laundry and the home robot could tell if the thing on the table was a can or a vase and put it back into its right place.
Our concept of time and place had changed immensely as mobile broadband gave us full and fast access to the internet no matter where we were. But when the chip reader was introduced as a standard element in most mobile phones, the change was even more significant.
Sofie Mustermann, who was about 10 years old at the time, still remembers having to explain to her parents that they could use objects in the real world in exactly the same way that they would use links on the internet; by pointing to it to call the information behind it.
As people moved about, they could get information on all the goods, buildings, machines, etc. in their surroundings if simply their mobile phones were close enough to the object to read its chip.
Another important advantage, that we may tend to forget today, is that things don't get lost anymore. In the old days, you had to go look for whatever you couldn't find, but today our multitude of chip readers make up a complete system that keeps track of anything with a tag on it - and that's pretty much everything. We need only do a online search - just like when we search for words or pictures on the computer.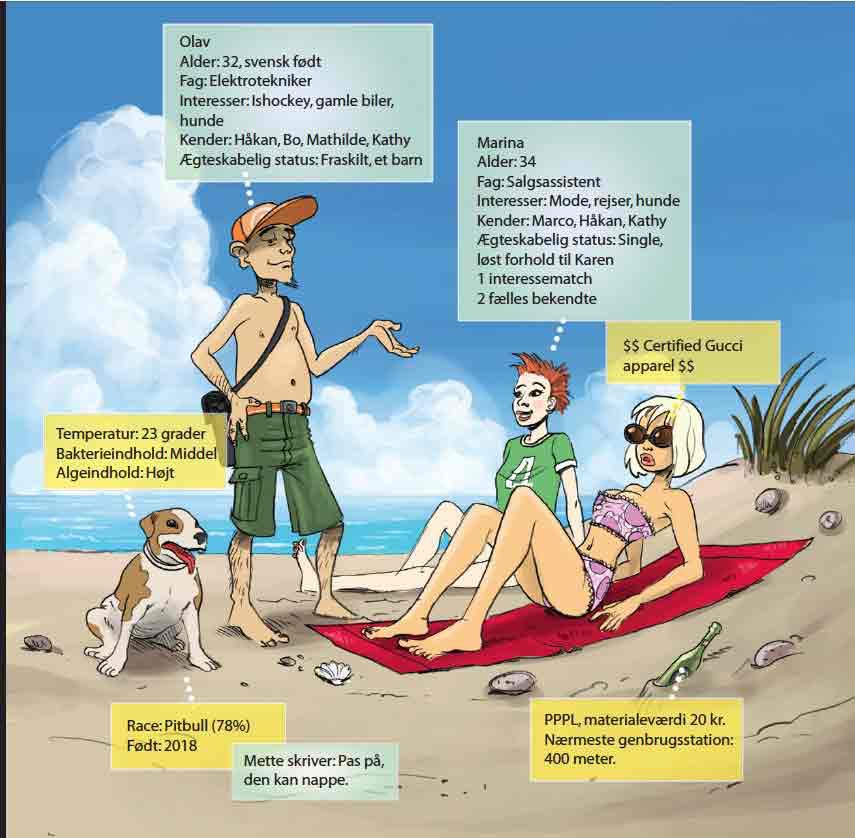
Technically, the ID implant was a logical continuation of the so-called RFID-chips that replaced the old-fashioned bar-codes on all kinds of merchandise around 2015. The process of change was a long and complicated one. All types of goods and merchandise, and in many cases sub components of some types of merchandise were fitted with an electronic circuit: a chip that would reveal its data once it was hit by the radio waves from a chip-reader.
The RFID chip is actually an extremely simple device. All it needs to contain is an ID number since the computer reading the number can easily look up any information relating to that particular number online. If the RFID reader reads the number on, say, a bottle of ketchup, the system can access all kinds of information relating to that specific bottle: the price, supplier, the manufacturer's website, recipes, declaration of contents, etc.
Let In or Keep Out
Around 2010, most stores and vending machines were accepting payment without the use of cash or credit cards. Instead, you would transmit payment via a chip in your mobile phone simply by typing a PIN code on the keypad. Once you had the chip in your mobile phone, you could use its code to open your door with, as an electronic ticket, or for paying at parking meters or soda machines in much the same way.
Gradually, as keys, credit cards, tickets and ID papers were fitted with RFID chips, it became increasingly clear that the most rational would be that each person had a single personal chip that could uniquely identify him or her in whatever aspects of life might be relevant. The mobile phone actually had that function for a couple of years, but it was a vulnerable solution, since loosing or forgetting the mobile phone posed tremendous problems to the owner.
Cats and dogs and other pets had been tagged with RFID chip implants for many years, but the idea of also tagging human beings like that was somewhat more difficult to accept - however logical and convenient it might seem in hindsight.
And certainly not everybody voluntarily accepted the implant to begin with. One of the first areas that started systematically RFID tagging of people was the prison system. Many prisoners were given a wristband or an electronic foot shackle that made it possible to constantly track their most minute whereabouts. In the prisons, it helped prevent attacks and drug dealings, because the wardens could now monitor who were with whom where and at which times. Outside the confines of the prisons, the electronic shackle made it possible for convicts to do time under restrictions in their own homes, just as it became possible to ban individuals from visiting certain areas, such as the neighborhood in which an ex-wife lived.
Actual implants won their first huge market in Latin America, which was already then suffering from a series of hijackings and abductions. Around 2010, politicians, high-ranking officials as well as the rich and famous and their families happily accepted the implanted chip which would make it much easier to track them down should they fall into the hands of rebels.
To begin with, the chip implants were marketed as a status symbol. Exclusive stores, posh restaurants, fancy nightclubs and first class lounges in airports introduced chip readers and offered chip implants to their regulars. Once the customers had the implant, the staff would custom design their services to match each customer's individual wishes and needs as registered by the chip, and the customers enjoyed all the special privileges of skipping waiting lines at the entrances, exits, check-outs, etc.
And vice versa, if you did not have a chip - or if it did not refer to a fat bank account - no doors would be open to you.
The acceptance of chip implants amongst ordinary citizens is largely due to the coordinated and target efforts of the Asian companies and authorities. The traditional European skepticism towards technology was never as outspoken in Asia. Quite on the contrary, in Korea, Singapore and the Chinese Pacific Areas, people enthusiastically welcomed the possibilities inherent in the chip.
The key word is convenience. Back then, the Asian electronics conglomerates had long since taken advantage of their special ability to interlink all their many different apparatuses into one coherent system based on the concept that everything - the air conditioning, bathroom scales, freezer, vacuum cleaner, car, etc. - should ideally be able share information and analyze their user's habits and needs on an ongoing basis.
Ghosts
We can do a search on everything and everybody that we meet. Checking everything has become our second nature: Has the sweater I consider buying been manufactured in accordance with my moral and ethical values? Let me just double-check what's available on our new job applicant - or on the guy who asked me out on Saturday.
But our lives have become equally transparent.
“Everybody else will be checking on us as well. The people we meet, negotiate with - all of them know a lot about us even before we meet. And we are not only being scrutinized by other people, Every gadget reading our chip can actually check on us, search databases or interlink with other gadgets to uncover everything we have ever said or done. We cannot even keep track of the extent to which we are being monitored: Where we are, what we buy, what we do, who we are with …” says Sofie Mustermann.
Italian anthropologist, Gianfranco Facadi, has demonstrated a quite new dimension in human interaction within the past couple of decades:
“Human beings have always paid much attention to their appearance. Clothes, jewelry and status symbols have been our means to signal who we are. Now, we are being evaluated and judged equally much by our digital appearance, our aura. Therefore, it is in fact quite natural for us to spend quite a lot of time nurturing and refining our profiles. We want to look good to whomever - or whatever - might be evaluating us.”
The reality, however, is that people have only limited possibilities to control their aura, as has been clearly demonstrated by the “Tagging” phenomenon.
“Tagging” means putting a mark on something, and it seems to have become the new game of the day. Enormous websites have been established where everybody can jot in comments relating to any object, person or place.
For instance, if you are very happy with the services offered by a particular store, you can add that comment on the tagging website - either by creating a new page or adding it onto an existing page. You can even expand you comment with links to point out that the same type of goods may be available at a better price elsewhere, for instance.
Others who consider shopping in the particular store can now study what has been written about it. In that way, you can actually discover an entirely new layer of any city. Whenever you go for a walk, you can get comments and information relating to everything you see on your way, or that may have been there in the past.
As Gianfranco Facadi puts it: past events will live on as digital information relating to a place or thing - hovering there forever like ghosts.
A transparent world
While it is probably right that nobody can mention one single aspect of our lives that is not being registered, it does not mean that everything is visible to everybody, explains Flemming Macht from the Home Office. He thinks that by using the international citizen account system, we are well equipped to control who can see what.
“The Citizen Account” was developed in a unique cooperation between the United States of America, the European Commission and Microsoft and much seem to indicate that the system will be accepted as the global standard.
The general principle is that every citizen can create a number of different accounts in which the numerous types of information and data are stored. The citizen will then define a list of accessors and contributors to each individual account. Spouses typically give each other full access to each other's accounts. The bank, public authorities, doctors, friends, employers or business associates are given access to various combinations of the accounts.
The citizen account is one of many - quite indispensable - tools by which you can control your presence. We call it “Presence Management”.
The constant contact to a global computer system that knows our identity has lead to an upsurge of communications. We are bombarded with requests from screens, robots and apparatuses that apparently know our interests, consumer patterns and financial status. Spam has been with us ever since the infancy of the internet, but gradually as everything has been uploaded to the internet, spam seems to be all over the place.
Our well-being and ability to focus have come to rely intensely on powerful and precise filters that can sort the enormous amounts of information that we receive.
Stig Rehn from the association called “The Devil's Brand” has often made quick-witted statements on the problems involved in the propagation of the ID chip - here's one quote to end this article:
“We don't have a choice! A system has been enforced upon us that leaves us open to whomever wants to spy on us. We may have our reputation spoiled by vandals who tag us with false information. We have lost our right to privacy, anonymity and uncommittedness. Yet, if we refuse to have the chip implant, we are by no means better off. Without the chip, we are selected for special controls, we are showered with special fees, and cannot get a job. It is convenient, yes - but we have become enslaved by our own master system.”
Text: Peter Hesseldahl